Companies that use SAP ERPs constantly develop new codes in the SAP ABAP (Advanced Business Application Programming) programming language to adapt and/or create specific functionalities to their business and process needs. As a result, they can accidentally or intentionally introduce security holes by exposing and making SAP environments vulnerable to hacker attacks.
If you don’t know the answers to the questions below, then you are likely in the risk group of companies that have custom ABAP developments “known as the Z program” and that are exposed and vulnerable to security breaches.
- Do you know how many builds ABAPs have been created for your organization, the purpose of each build, and whether all of them are actually being used in production by business users?
- Does your company have an ABAP development policy that incorporates security practices and risks to mitigate the most known vulnerabilities and breaches?
- Does your team of developers or company contracted for ABAP developments follow the security and risk practices adopted in your company’s development policy?
- Does your company have the mapping and control of customizations that expose your business to risk (including the identification of the main mapped vulnerabilities and procedures to reduce identified risks)?
- Do your custom codes have the minimum restrictions necessary to comply with the LGPD Law?
A well-developed ABAP code must incorporate mechanisms that can avoid vulnerabilities and security breaches such as SQL INJECTION, ABAP CODE INJECTION, ABAP COMMAND INJECTION, HARD CODED USER AND PASSWORD, SOD RISK RELEVANCE, SAP NON-COMPLIANCE ABAP CODING, SENSITIVE DATA ACCESS ( compliance with the LGPD law) etc.
Every company should have an ABAP development policy that incorporates safety and risk practices, and this policy should be part of the internal development process and the process of hiring and qualifying third-party companies contracted to work on ABAP developments.
To mitigate the risks mentioned above, you must first inventory your ABAP customizations and their vulnerabilities. Subsequently, determine immediate corrections, such as adding the programs and, consequently, the customized transactions considered critical to your SoDs segregation of duties (Segregation of duties) risk matrix. You can also make use of the SAP ABAP Test Cockpit (SAP ATC) solution to automate the code verification and approval process during the “transport” release to the approval environment. SAP ATC is embedded in the SAP Netweaver platform and you are certainly already licensed to use it at no additional cost.
Example of SAP ATC solution with FIORI interface (TrustSis exclusivity)
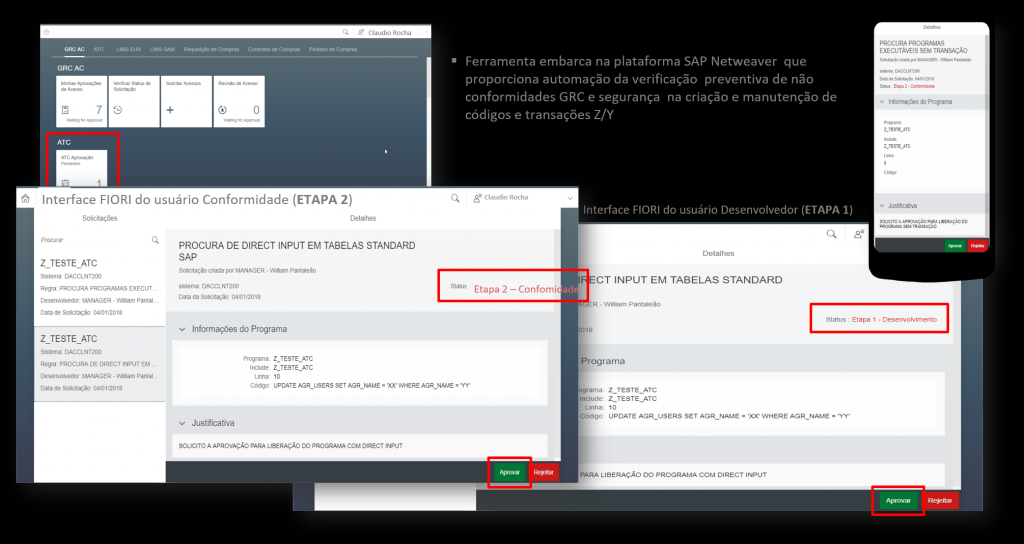
If you need more information about inventory services and security analysis, customization risks and how to make use of the SAP ATC tool (approval flow with Fiori interface), schedule a conversation with us!

