Cyber-attack threats are among the greatest risks facing organizations today. Discover the solutions embedded in the SAP platform “that do not require licensing” and that can help you in your Cyber Security strategy SAP / GDPR / LGPD.

General Description
SAP systems are not preconfigured by default with the most widely used security practices. As a result, SAP environments become exposed to a number of cyber risks from internal and external threats, which seek to manipulate the integrity of SAP environments, its transactional data, logs and sensitive data. Hackers have knowledge about these characteristics of SAP systems – which by default do not bring the most used security practices – and are exploiting these vulnerabilities to achieve their goals, manipulating and obtaining sensitive data.
Below are the main SAP security threats:
- Malicious code in ABAP development (Z/Y);
- SAP Security patch notes not applied;
- Unsafe open text data traffic;
- Default passwords / Simple passwords;
- Insecure RFC communication;
- Insecure web communication;
- Insecure user authentication;
- Exposure to sensitive data (GDPR / LGPD).
The SAP platform has embedded tools and mechanisms that can help in the cyber security strategy.
CONCERNED ABOUT THE INFORMATION SECURITY OF YOUR SAP SYSTEMS?
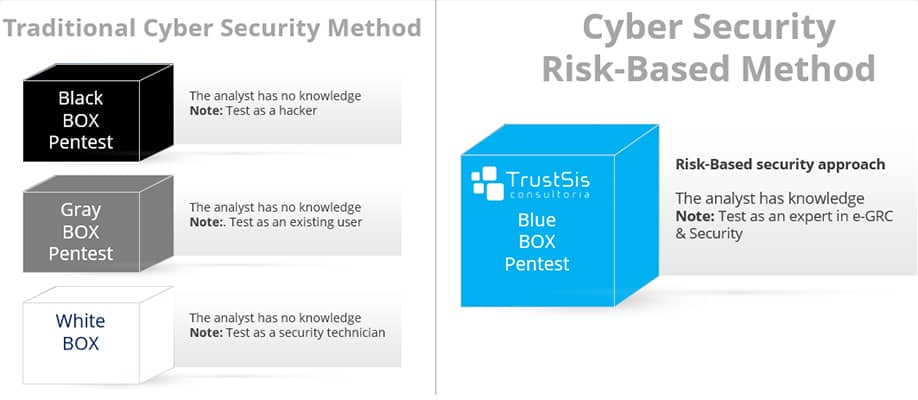
There are different strategies for the Pentest process in the context of Cyber Security for SAP systems. Traditional methods are oriented to Black, Gray and White BOX penetration testing. TrustSis developed the Risk Oriented Blue BOX Cyber Security method.
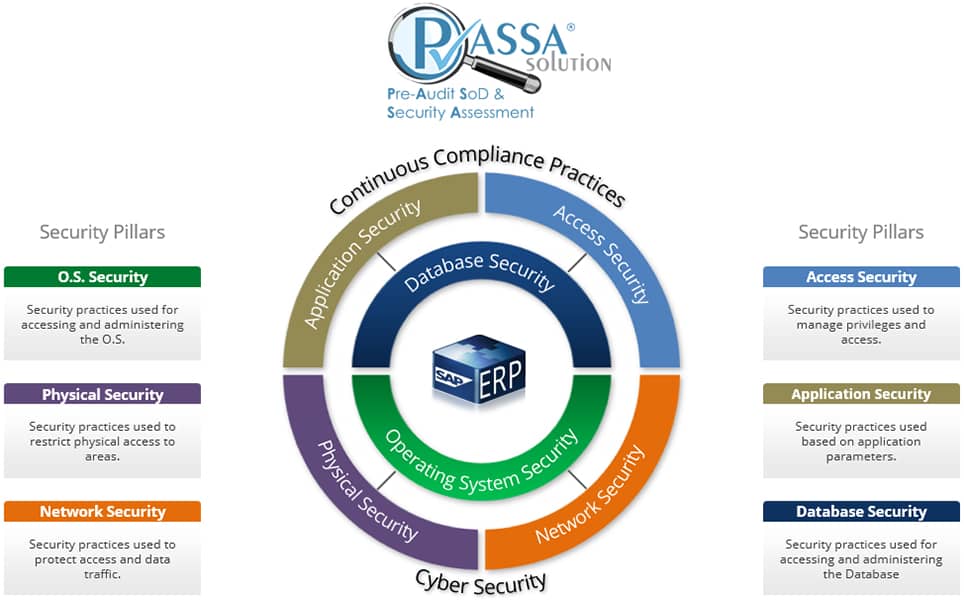
P.A.S.S.A. – DEVELOPED BY THOSE WHO MAKE COMPLIANCE THEIR OWN BUSINESS
TrustSis has developed a method to help companies anticipate situations of non-compliance with audits and internal GRC practices. PASSA – Pre Audit Security and SoD Assessment is essential to avoid those unwanted audited GAPs!
For each non-conformity identified by PAASA, a macro plan of good practices will be presented, which will include the following information:
- Non-compliance identified
Macro view of the procedures used “AS-IS”; - Corrective action plan
Macro view of best practices recommended for correcting non-compliances; - Estimate of time and resources involved
Macro view of corrective action activities, time needed for correction and people / areas involved.
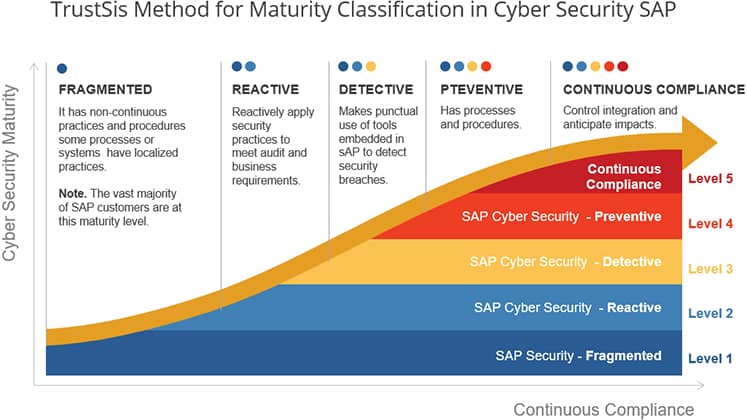
TrustSis Method for Maturity Classification in Cyber Security SAP
How we help our customers
Process and platform domain
Faced with constant innovations in practices and systemic solutions, you don’t have to worry. We are specialized and prepared to recommend the best processes and platform to address your requirements and challenges.
Implementation of the right measure
All processes are modeled observing GRC requirements and safety practices, internal policies, regulations, etc. We carry out the configurations of the adopted solution seeking to improve the user experience and reduce the operational cost of the process.
Support and Sustention
We offer specialized AMS support services for operating and sustaining the established process. We have a team trained in the process and solution, and differentiated methods and practices for service and continuous compliance assurance. COMPLIANCE OPERATOR support. A TrustSis exclusive!
