How to build an effective GRC process for SAP Security and Access?
Regardless of the business segment, it is a fact that all private or publicly traded organizations seek to establish the best Governance, Risk Management and Compliance (GRC) practices for their business processes.
Considered the basic pillar of GRC control, the access management process in organizations is the one that most causes divergence as it is a process that requires the engagement of multiple areas, such as: IT Security and Access, Governance, Internal Controls, Audit, Risks and business areas.
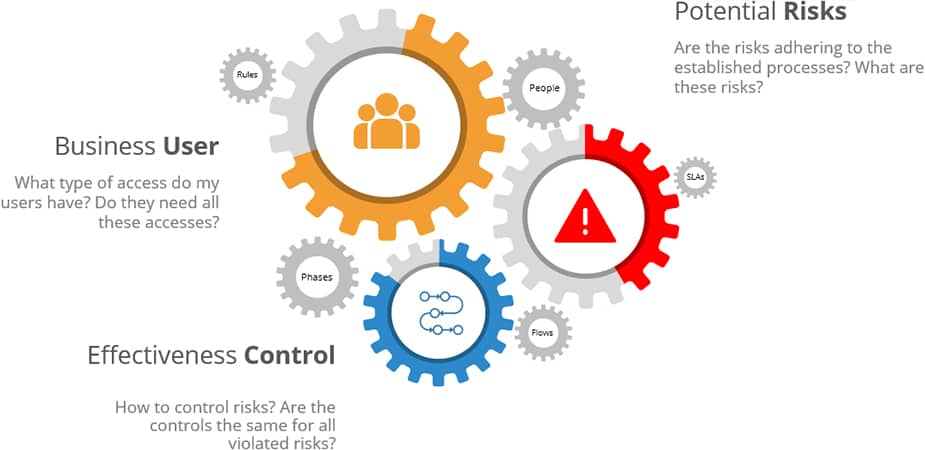
AN EFFECTIVE GRC PROCESS FOR ACCESS CONTROL REQUIRES EVERYONE’S ENGAGEMENT
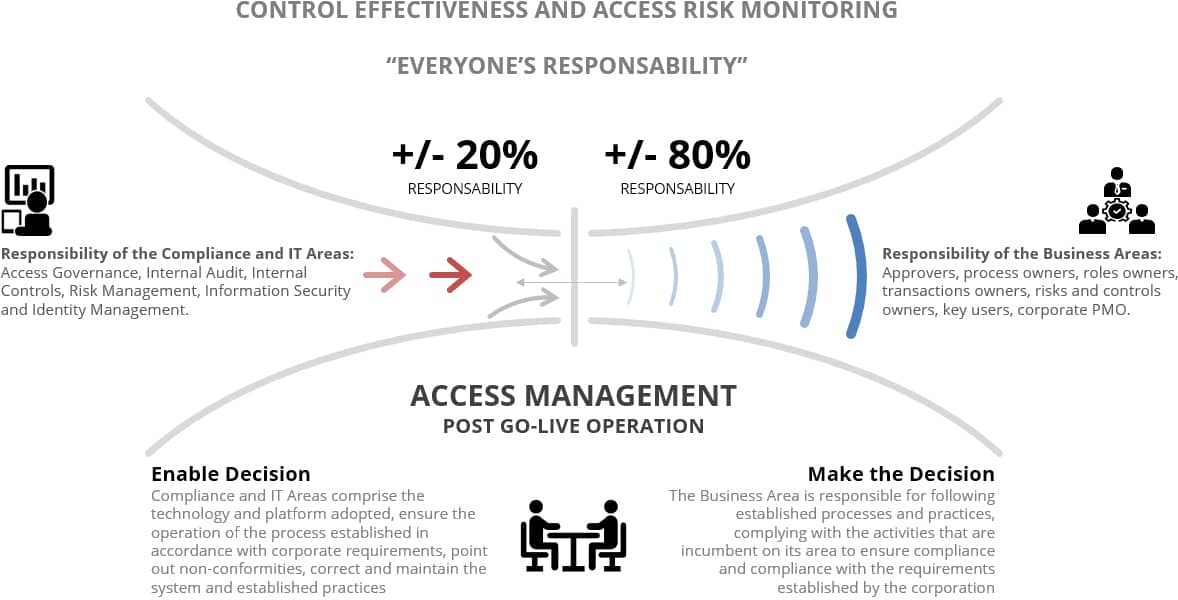
MAIN KNOWN PROBLEMS IN THE PROCESS OF ACCESS CONTROL AND RISK MONITORING SODs IN COMPANIES
Need an effective Access Management process, namely:
- Governance Model and Corporate Profile Management (Business and IT) – On-going;
- Definition of Roles and Responsibilities;
- Adoption of a systemic GRC platform;
- Definition and publication of the organization’s policies and regulations;
- Others.
IT cannot effectively support the process of access control and monitoring of SoDs Risks alone

MAIN TECHNICAL DEFINITIONS
- PROFILE OWNER (ROLE OWNER), person responsible for assessing the risks and approving profile requests that are their responsibility. It is also responsible for requesting and approving profile adjustments according to business requirements.
- TRANSACTION OWNER, person responsible for assessing the risks and approving requests for transactions that are their responsibility. It is also responsible for requesting and approving adjustments to transactions in accordance with business requirements.
- RISK OWNER (RISK OWNER), person responsible for defining and determining the best risk structure capable of identifying the risks of access attributed to users. It also recommends and approves adjustments to the SoD risk structure according to business requirements.
- CONTROL OWNER (CONTROL OWNER), person responsible for defining and determining the best compensatory control option capable of reducing or eliminating the risks of access attributed to users. It also recommends and approves adjustments to compensating controls in line with business requirements.
- RISK MONITOR (RISK MONITOR), person responsible for monitoring and also receiving notifications of violated and materialized risks. It needs to assess and determine the root cause and evidence decisions that may refer to acceptance of the breach and materialization of risk, or transfer of risk to another person.
- APPROVER (APPROVER), person responsible for approving access requests from users under its responsibility. It must also assess the risks arising from the requests for access being approved and make it aware that it recognizes the legitimacy of the risk.
- KEY USER (KEY USER), person with functional knowledge of the business process. It also supports the definition of access profiles and validation of access restrictions, executing business scenarios with the purpose of validating that there is no interference (less or more access) to carry out business transactional activities. Request profile adjustments when necessary according to business requirements.
THE USER’S EXPERIENCE IN THE ACCESS APPROVAL AND REQUEST PROCESS MAKES ALL THE DIFFERENCE WHEN SEEKING THE BEST ENGAGEMENT OF ALL
SAP has incorporated SAP Fiori’s modern design into its products so that users can enjoy a consistent experience from start to finish. SAP Fiori is part of the SAP platform solutions for Governance, Risk and Compliance (GRC), which includes the SAP GRC Access Control (SoDs access management and risk monitoring solution). With the use of SAP FIORI interfaces for GRC, the SoDs Access Management and Risk Monitoring processes increase their acceptance by employees due to an appealing and customized design tailored to each task.
Examples of FIORI Apps for SAP GRC Access Control
![]()
End User | Managers | Administrators | Reports




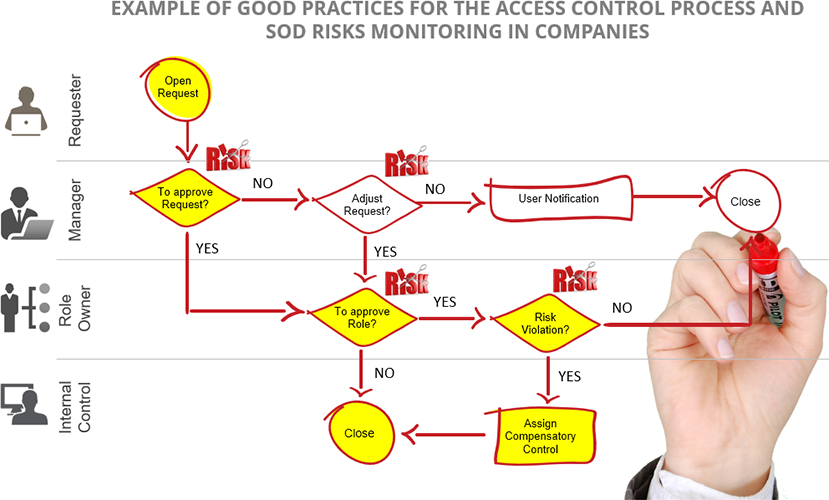
EXAMPLE OF GOOD PRACTICES FOR THE ACCESS CONTROL PROCESS
AND RISK MONITORING IN COMPANIES
How we help our customers
Process and platform domain
Faced with constant innovations in practices and systemic solutions, you don’t have to worry. We are specialized and prepared to recommend the best processes and platform to address your requirements and challenges
Implementation of the right measure
All processes are modeled observing GRC requirements and safety practices, internal policies, regulations etc. We carry out the configurations of the adopted solution seeking to improve the user experience and reduce the operational cost of the process.
Support and Sustention
We offer specialized AMS support services for operating and sustaining the established process. We have a team trained in the process and solution, and differentiated methods and practices for service and continuous compliance assurance. COMPLIANCE OPERATOR support. A TrustSis exclusive!
