THE WEAKEST LINK IN INFORMATION SECURITY IS PEOPLE!
People’s login access, although not the only weak link in information security, is certainly one of the most important. This importance increases relatively with the number of different systems that people need to perform business activities in a corporate context.
The fact is that most companies still do not have a single login mechanism to facilitate the process of authenticating users to the different systems they may need to access every day. With this, users intending to make their day-to-day easier use weak passwords, certainly the same for all systems that need to login and in the worst case scenario they store their passwords in the famous piece of yellow paper under the keyboard.

HOW TO IMPROVE THE USER EXPERIENCE IN THE LOGIN PROCESS IN SINGLE SIGN-ON (SSO) SYSTEMS

Having an information security process that establishes strong passwords, password expiration date cycles, and systemic password change mechanisms may not be the only desired solution; it can even increase the operational cost of the process as a result!
The best option to eliminate part of the problem related to user login and high operational cost with password change process is to establish the Single Sign-ON (SSO) mechanism.
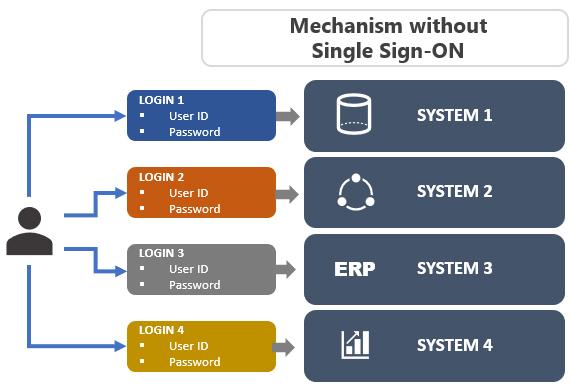
Common issues with user login without single sign-on mechanism:
- Multiple passwords due to different systems;
- Passwords are written on paper and kept in an easily accessible place;
- High volume of requests to unlock and reset passwords;
- User idle time due to blocked access;
- High operational cost in the process of unlocking and resetting passwords;
- Weakened Information Security.
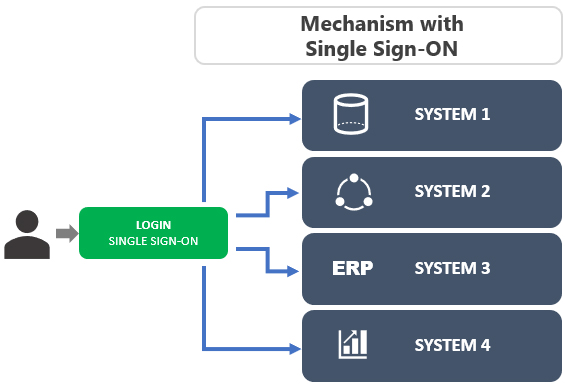
Main advantages of using the single sign-on mechanism:
- Eliminates the need for multiple passwords across different systems;
- Passwords are written on paper and kept in an easily accessible place;
- Eliminates or reduces request volume for unlocking and resetting passwords;
- Eliminates or reduces user downtime due to blocked access;
- Reduces operational cost in the process of unlocking and resetting passwords;
- Adherent to digital transformation trends;
- Improved Information Security.
How we help our customers
Process and platform domain
Faced with constant innovations in practices and systemic solutions, you don’t have to worry. We are specialized and prepared to recommend the best processes and platform to address your requirements and challenges.
Implementation of the right measure
All processes are modeled observing GRC requirements and safety practices, internal policies, regulations, etc. We carry out the configurations of the adopted solution seeking to improve the user experience and reduce the operational cost of the process.
Support and Support
We offer specialized AMS support services for operating and sustaining the established process. We have a team trained in the process and solution, and differentiated methods and practices for service and continuous compliance assurance. COMPLIANCE OPERATOR support. A TrustSis exclusive!
