SAP Cyber Security
Prevention is cheaper and much better than make treatment, say all those who have gone through difficulties, whatever the scope. Thinking about it and adding an extremely relevant fact, reported in all the media, when an important cyber attack occurred, in one of the largest retail chains in Brazil, we really need to invest in prevention and in the care that a secure IT environment requires.
Everyone was scared and worried about what happened, CSO, CIO, CTO, CEO, Managers, Directors, or even someone who is responsible for the IT security of any company, and, on one point, everyone agrees:
It is ell known that most cyber intrusions or data leaks are related to human errors. Organizations’ employees, in most cases, provide unintentional security breaches in different ways.
As experts in SAP Security, let’s address how this topic affects SAP systems
The most frequent gaps identified in SAP’s ERP systems are related to systems outdated in relation to security patches provided by the manufacturer; business users with unnecessary privileges; poorly defined system configuration parameters; end users information security policy in relation to their responsibility for protecting IT assets (eg password and data sharing); and last but not least, the lack of knowledge of systems administrators about the security architecture provided in SAP solutions.
The Human Factor and its Main Security Faults in SAP Environments.
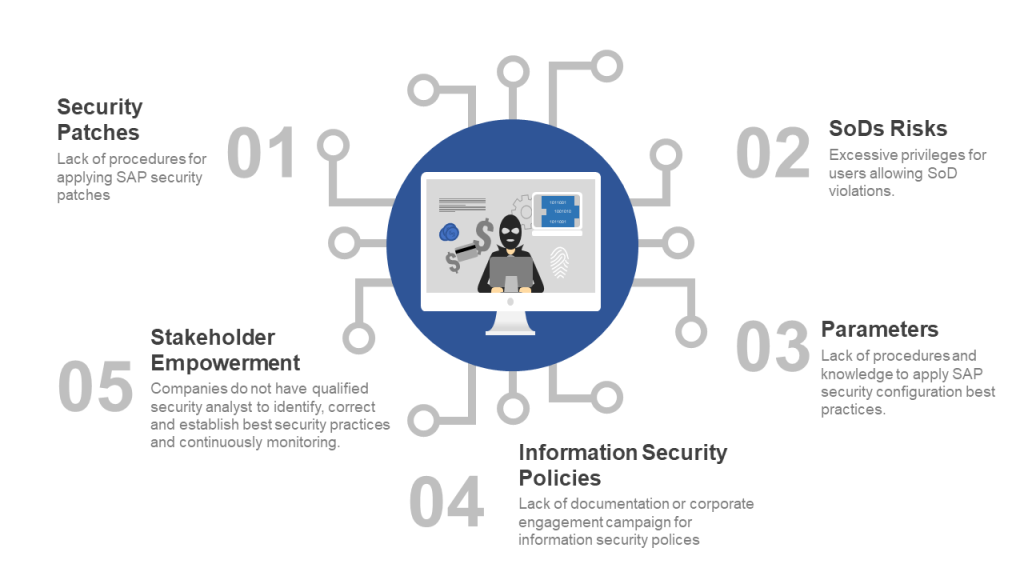
Several research institutes note the continuous growth of cyber attacks in organizations and point to the human factor as the weakest link in this scenario. SAP ERP systems are not immune to cyber attacks, on the contrary, they are starting to appear more frequently, especially because of the increased exposure of these systems to the Internet.
Currently, most companies that use SAP systems have projects in progress or are executing a strategic migration plan for S/4HANA. The search for hosting alternatives for SAP ERP systems in the cloud is becoming more frequent in view of this market trend and the benefits that the model provides, in terms of cost and accessibility. With SAP ERP applications in the cloud, users access production environments using Internet browser and, mainly, through FIORI apps. Faced with all this technological improvement and, therefore, a paradigm shift in relation to the architecture and platform SAP in the cloud, it`s important not to forget the minimum recommended security practices.
And here comes the question: Is your organization treating SAP information security with due attention?
The relationship between people and successful cyber attacks

The figure below lists the main SAP solutions for the SAP Information Security. The alternative security tools and solutions provided by SAP are not limited to those mentioned below. For example, the SAP Netweaver and SAP HANA platforms together offer a wide variety of tools, protocols and embedded mechanisms (no licensing required) that support the establishment of the minimum information security practices necessary for SAP ERP systems considered critical for organizations.
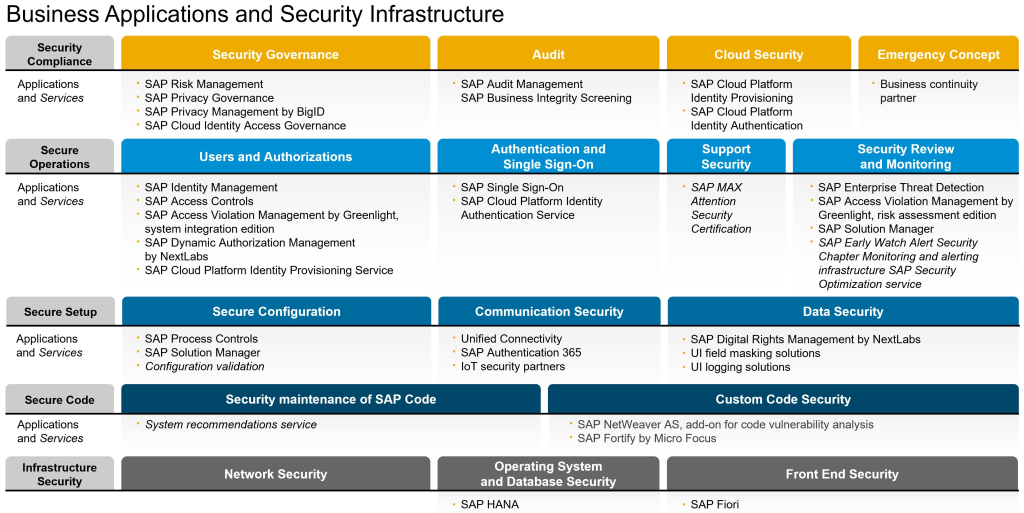
Cyber attacks on SAP ERP systems can be prevented or avoided in many cases with simple actions that involve, for example, obtaining knowledge of the security architecture embedded in SAP solutions and putting them into practice. You can find on SAP website detailed information about tools embedded in the platform (no licensing required), configurations, parameters and protocols that support information security best practices. To make it easier, SAP has a security map that illustrates the different layers of security. The figure below shows the most up-to-date version of the security map provided by SAP and it is possible to visualize the different areas in the security context covered by each layer.
Security Map
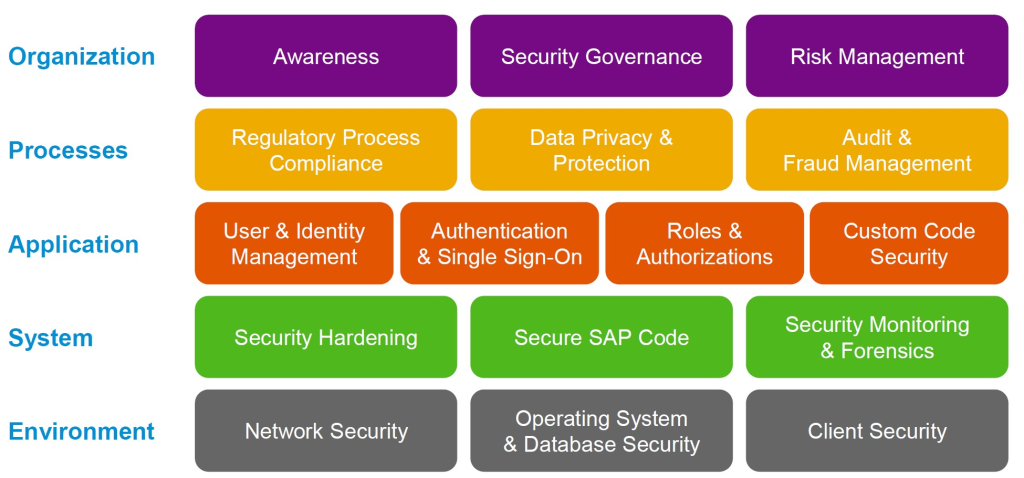
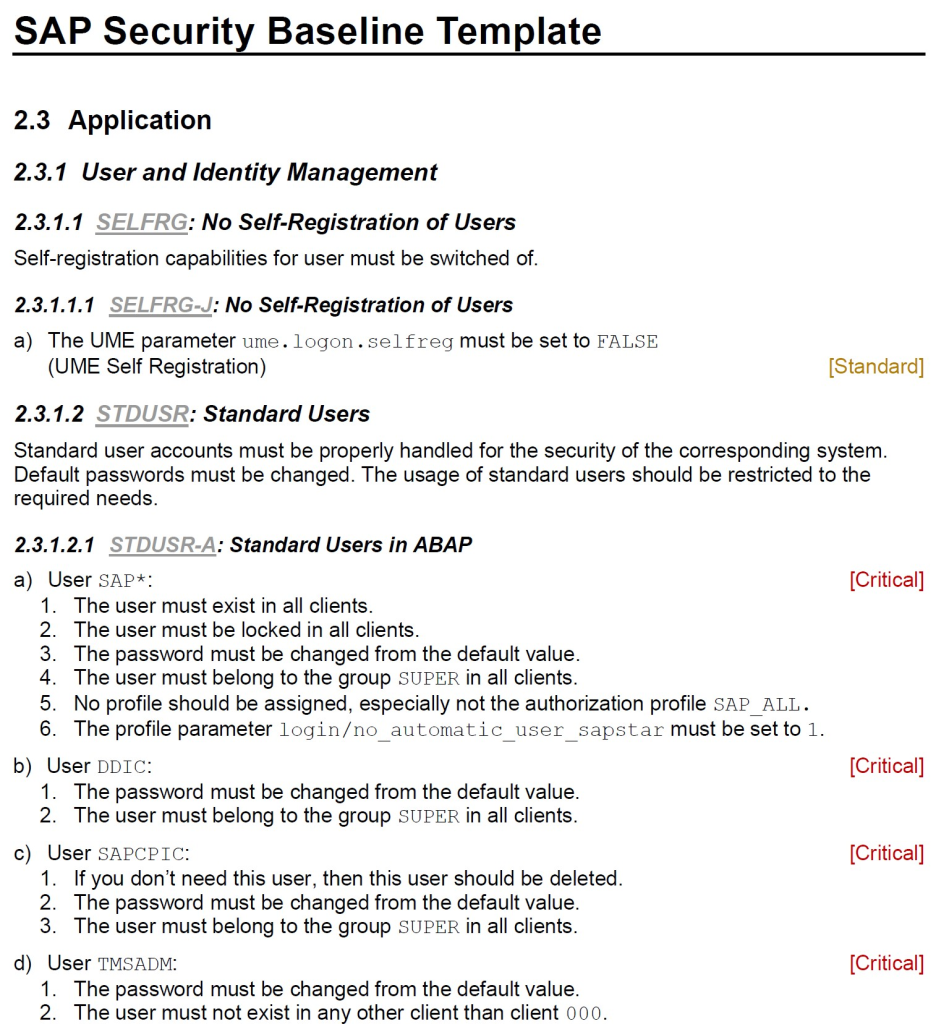
The security map presented above is part of the “SAP Security Baseline Template” which is a template document provided by SAP to support organizations in defining structured security practices. The document includes the minimum security practices recommended by SAP for the different security layers presented. To download the latest version of the document, access to the SAP note and click on the links – Note 2253549 – The SAP Security Baseline Template
A simple action to reduce exposure to cyberattack risks on SAP ERP systems is to make use of the security practices presented at the document “Security_Baseline_Template_V2”, available in SAP Note 2253549. The document describes security aspects for each layer of the security map with technical details about configuration parameters and their relevance rating (Critical, Standard and Extended) for the system.
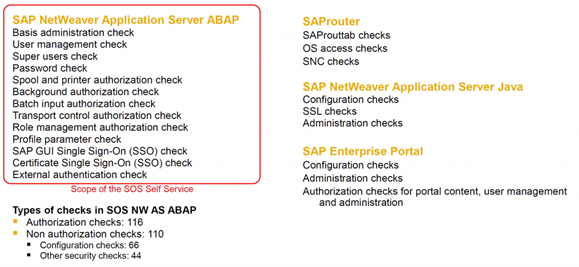
Another tool embedded in the SAP platform (no licensing required) that greatly contributes to the process of reducing exposure to cyber-attack risks in SAP ERP systems is the SAP Security Optimization Service – SoS solution. This solution performs analysis of approximately 200+ risk indicators related to information security, the final report presents technical details of each identified vulnerability, risk classification in High / Medium / Low and action plan recommendation to identify the root cause and mitigate the problem.
Briefly, not always the best option to go looking for the best security system or hardware for the answer to your security incident. Based on statistics, a good part of cyber attacks and information leakage occurred by human error, from inside to outside of organizations, as a result of misuse or lack of knowledge of the security mechanisms present in the SAP platform.
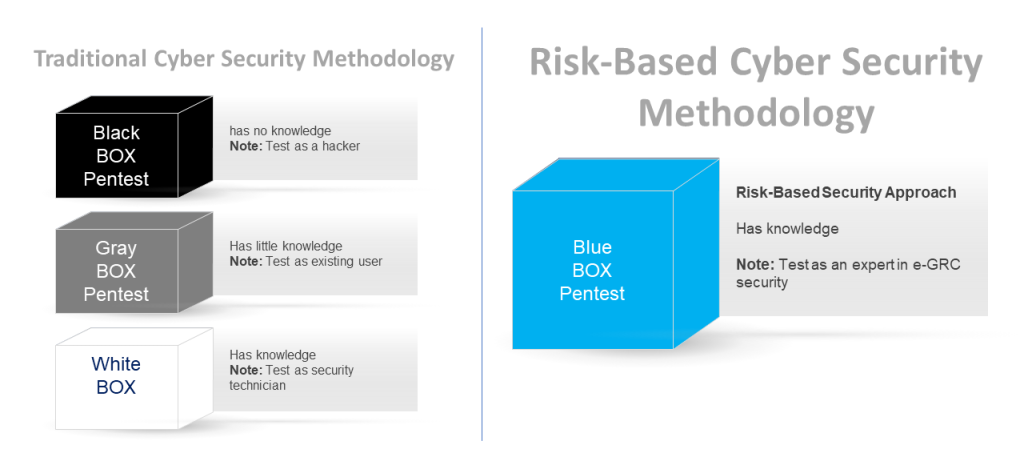
TrustSis is the unique specialized and niche company in SAP security in Brazil, with know-how, method and solutions to help companies reduce these security GAPs pointed out in this article. We have developed our own method, called TRUSTSIS BLUEBOX, which provides an alternative for SAP customers to run a PenTest specialized in SAP. Want to know more, contact us!
– Here are examples of our BlueBox method and how we rate security maturity in an organization.
TOP 5 TIPS TO HELP IN SAP SECURITY STRATEGY
- Eliminate unnecessary privileges for all users of SAP systems.
Identify Segregation of Duty Risks (SoDs) in users and clean up as soon as possible.
- Check the communication interfaces with your production system.
Many RFCs have unnecessary SAP_ALL privileges.
- Establish a basic security procedure for new SAP developments.
Companies are not paying attention to the risks posed by insecure coding, especially if they are exposed on the internet via Fiori apps, etc.
- Map the SAP IT architecture to information about all trust relationships between systems, access mechanism used by users, active security protocols, etc. and determine if the minimum security settings recommended by SAP are active.
- Establish continuous monitoring procedures using embedded tools and solutions (no licensing required) on the SAP platform, for example, RSecNotes, SAP SOS, SAP ATC, SAP RAL, SAP Solman etc.)

