SAP S/4HANA – THIS IS THE TIME TO GET THE SECURITY YOU WANT IN YOUR ACCESS PROFILES!
SAP S/4HANA deployment using Greenfield, Brownfield or Bluefield approach, what does this influence on access profiles?
The strategic definition of migration from SAP to SAP S/4HANA considers several scenarios including the advantages and disadvantages of each one of them in relation to the method that will be used.
The “user profiles” aspects of authorizations are also part of the scenarios that determine the most suitable method of migration. The implications of permits, ie; the way in which user profiles will be impacted as a result of the choice between the best known ‘Greenfield, Brownfield or Bluefield’ models certainly does not determine the choice of the model itself, however, it is good to know what these implications are, including its advantages and disadvantages in relation to adopted model
It is a fact that SAP S/4HANA goes beyond a technical upgrade, the HANA platform is full of functional and technological innovations that allow, among other things, a new experience for users through FIORI apps, simplifies the structure of tables and consequently transforms access and more dynamic and faster processing.
All these improvements and innovations provided by S/4HANA mentioned above also required significant improvements in the architecture of SAP authorizations “Profiles”.
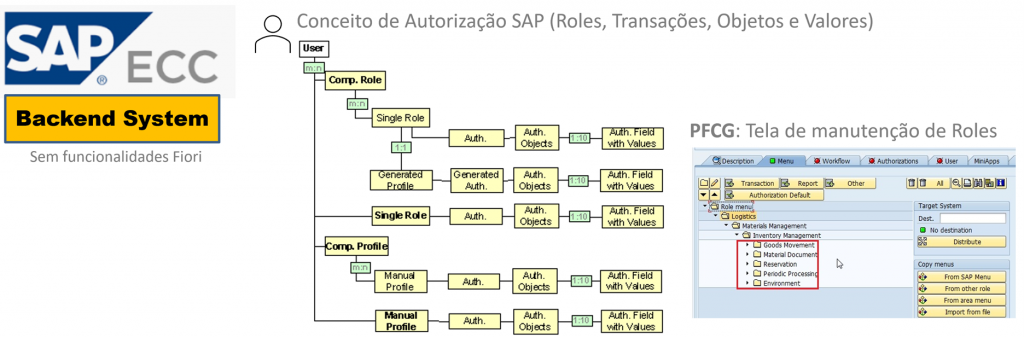
The traditional authorization concept for SAP ECC systems and earlier versions (SAP Netweaver ABAP Platform), are structured to protect transactions, programs and services against unauthorized access.
Obs. The figure below illustrates the example of traditional authorization architecture (profiles) that we know today!
The S/4HANA authorization concept is very similar to the traditional structured authorization model to protect transactions, programs, services from unauthorized access. The difference is basically due to the inclusion of FIORI technology that improves the user experience with the use of FIORI Apps.
Note The figure below illustrates the example of S/4HANA architecture
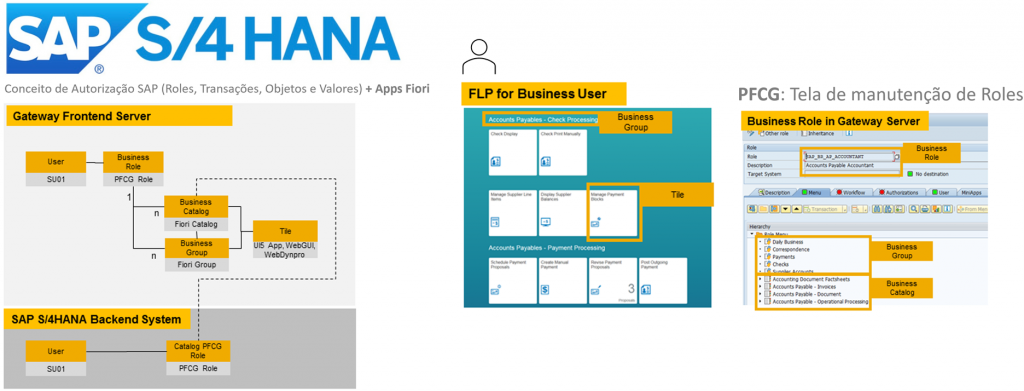
Image source: sap.com
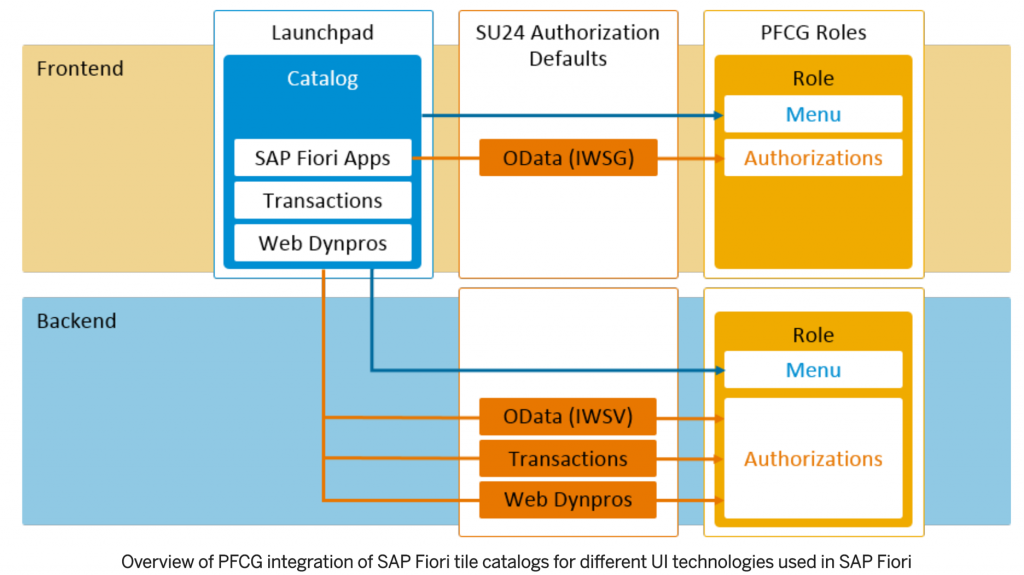
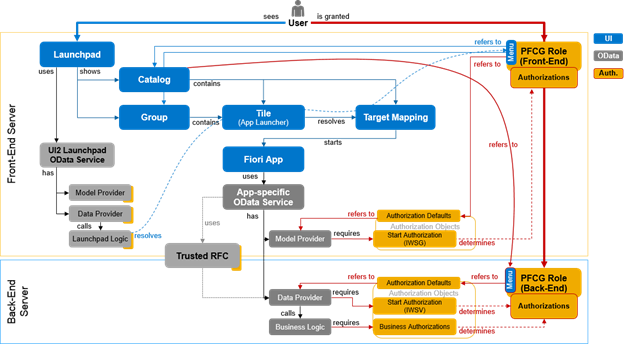
Translating all the innovations that occurred in the S/4HANA authorization architecture (Profiles) into a technical view, the drawing below illustrates the main access required by a business user using Launchpad FIORI and its relationship with profiles and access restrictions that we are accustomed to dealing on a day-to-day basis (PFCG).
The drawing below shows a higher level view of the main attributes involved in security aspects compared to the technical view illustrated above.
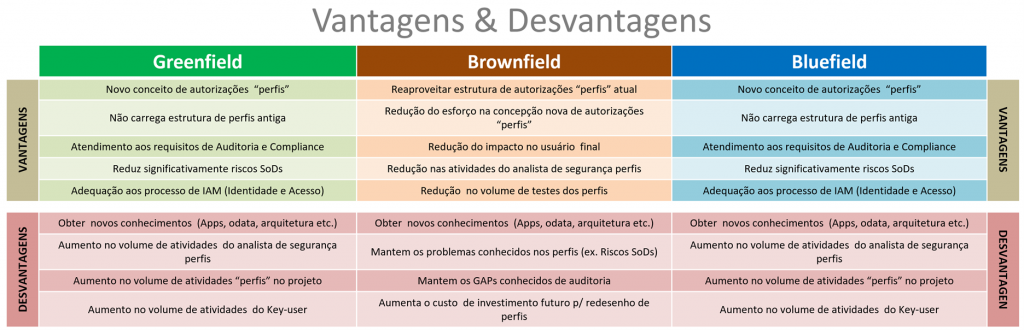
GREENFIELD, BROWNFIELD OR BLUEFIELD APPROACH, WHAT DOES THIS INFLUENCE ON ACCESS PROFILES?
Migration Model S/4HANA – Greenfield (impact on SAP authorization “profiles”)
By adopting this Greenfield migration model, the structure and concepts of SAP authorizations “profiles” can be designed and defined so that the concepts of using FIORI apps are incorporated and also to meet the audit requirements as well as GRC compliance (example: reduction of SoD risks – Segregation of Function). Note. The adoption of this model implies carrying out a new SAP implementation, and this also gives the opportunity to devise a more effective profile model from the point of view of security, auditing and SoDs risks – Segregation of function.
Migration Model S/4HANA – Brownfield (impact on SAP authorization “profiles”)
By adopting this Brownfield migration model, the current SAP “profiles” authorization structure will be kept the same, and during the migration process the profiles will be updated with new transactions, objects and the possibility of including new FIORI apps. These profile adjustments will be tested to ensure that users have all the necessary authorizations to perform their activities after migration. Note. Even if this model is adopted, it is still possible to incorporate in the project strategy the practices to meet the audit requirements as well as GRC compliance (example: SoD risk reduction – Segregation of Function).
Migration Model S/4HANA – Bluefield (impact on SAP authorization “profiles”)
By adopting this Bluefield migration model the SAP authorization structure “profiles” can be kept the same with all the possible problems mentioned in the Brownfield method. On the other hand, the Bluefield method offers customized tools that automate the migration process, allowing you to select data, configurations and customizations. The structure and concepts of SAP authorizations “profiles” can then be conceived and defined to incorporate the concepts of using FIORI apps and also to meet the audit requirements as well as GRC compliance (example: SoD risk reduction – Segregation of Role).
 TOP 8 TIPS TO HELP WITH THE S/4HANA SECURITY STRATEGY
TOP 8 TIPS TO HELP WITH THE S/4HANA SECURITY STRATEGY
- No tool to help identify problems with lack of access consolidates all the information needed to determine the solution to the problem. It is sometimes necessary to browse all or several of them to determine the root cause of a lack of access problem.
- Remember that the S/4HANA user must exist with the same ID on the front-end and back-end system.
- Not all access failures are related to “profiles”. The error could be in the catalog, group or service.
- The time taken to identify access failures that use FIORI apps is greater than the time taken to identify access failures that do not use FIORI apps. Note Remembering that there are new tools made available by SAP to determine the root cause of a problem of lack of access.
- FIORI catalog can be shared in derived profiles.
- Take advantage of the S/4HANA migration time (regardless of the chosen model) to create the best structure of access profiles in order to:
- Reduce SoD Risks – Segregation of Function
- Reduce Security and Audit Gaps
- Establish more appropriate nomenclature for SAP IdM integration – IAM processesM
- Make profile reuse more flexible
- Establish governance policy in ABAP development
- Incorporate authority-check into developments
- Preemptively mapping risks and vulnerabilities in codes
- Preventively identify the Z/Y transactions that need to be in the SoDs Risk matrix
- For those who opted for the Greenfield method, this is the time to gain control over the security of the customizations with a well-designed ABAP security and governance policy.
- Establish a security architecture considering the new landscape
- Establish trust for cloud applications
- Ensure secure access for users coming from the internet through FIORI interfaces
- Establish secure communication between SAP and non-SAP Systems
- Assess LGPD/GDPR privacy aspects with information exchange between systems and hosting of systems in providers of these services.