The best SAP profile template
The best SAP access profile template for your organization is the one you don’t realize exists. Discover the secrets to obtaining a good SAP access profile model.
The “One model fits all” SAP access profile model does not exist. Be suspicious when someone recommends an access profile model like “Job Position for example” without first having assessed your organization’s main requirements such as; procedures and access management platform adopted, GRC practices required by the audit area, internal controls and security, process maturity, current culture of the organization, etc.
Advanced Knowledge is Essential
Obtain a model of SAP access profiles that adheres to the organization’s business and at the same time does not cause problems for the IT area such as: non-compliance with Audit and Security practices, exposure to SoD Risks (Segregation of Duties), lack of control in governance aspects, high operational cost for operation, support and support of the adopted access model, etc., in fact requires advanced knowledge of the SAP authorization architecture (including S/4HANA) and practices for identifying the main factors and organizational requirements.
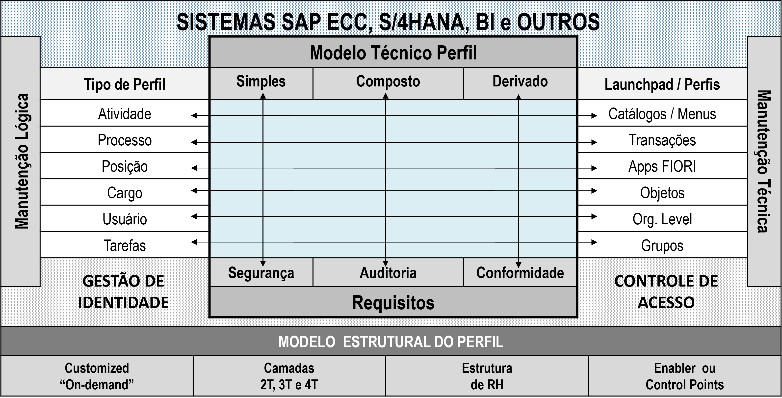
Figure 1: SAP Authorization Architecture Complexity (Profiles)
Some fundamentals associated with the authorization architecture present in the main Netweaver-based SAP products (ABAP) are only acquired in practice. The figure above illustrates the main technical attributes that SAP access profile specialists must know to develop and propose access profile models for an organization.
Three Pillars for Success
Observing the complexity and flexibility present in the authorization architecture of the SAP Netweaver platform (ABAP), security specialists and SAP profiles must include in their strategy at least the 3 pillars below, considered fundamental for defining, preparing and proposing a profile model and structure adequate access for the organization: they are:
Pillar 1: Technical Structure – Pillar for evaluating the quantitative relationship of the number of profiles vs. number of transactions vs. number of authorizations provided by the ideal profile model.
- Number of profiles generated;
- Number of Duplicate Transactions/Authorizations;
- Amount of unnecessary access granted;
- Number of Roles associated with the End User.
Attention point. It is common to see companies that use SAP systems use the relationship between the number of access profiles and the number of active users existing in the SAP system as a metric and factor for judging the quality of the profile model adopted by their organizations. Using this metric alone is practically making an assessment error. Other important factors must be considered to evaluate a good access profile model. It is not correct to evaluate a profile model as bad simply by comparing the significantly greater number of SAP access profiles in relation to the number of users in the environment.
Pillar 2: Risk Management – Pillar for assessing aspects of adherence to security, auditing, internal controls and risks requirements provided by the adopted model:
- Simple Profiles without Violation of SoDs risks;
- Flexibility for managing SoDs Risks;
- Access Security;
- Request vs Provisioning additional access.
Attention point. The vast majority of SAP access profile construction and/or redesign projects aim to obtain as a final product (because they are measured as such by the customer) the reduction or elimination of exposure to SoD Risks in active business users. However, an important part of this process is modeling and establishing a governance process that provides the operating conditions supporting the proposed access profile model. This means that the idealized access profile model must be flexible enough to absorb the changes inherent to continuous improvements of ERP systems without suffering the impact (or at least reducing it) with the emergence of exposure of new SoD Risks, granting of unnecessary access or duplication, etc.
Pillar 3: Governance / Operation – Pillar for evaluating the model adopted post-project (operation and support) and its adherence to aspects related to maintenance costs and operational governance:
Naming convention that facilitates the request for additional access;
- Additional access maintenance flexibility;
- Flexibility for Organizational Restructuring;
- Flexibility for Rollouts;
- Flexibility to associate owners with profiles;
- Flexibility to incorporate exceptions;
- Flexibility in adhering to the GRC platform adopted for access management.
Attention point. Idealizing a profile model that absorbs the changes inherent to continuous improvements to ERP systems guarantees the return on investment (ROI). It is common for companies using SAP ERP systems to have recurring problems with access profiles related to audit GAPs, exposure to SoDs risks, etc. The fact that the idealized profile models did not observe the 3 pillars above to foresee in the profile model that anticipates such situations. Consequently, companies suffer from the recurrence of audit GAPs, year after year, with the topic of profiles recurring on the agendas of IT managers.
Adaptation is the Key
The figure below is a comparative analysis between profiles modeled by position (Job Position) and profiles modeled by tasks (Task Based). The cells in yellow highlight the negative points of the profile model adopted based on the assessment pillar / Requirements identified and assumed by our example. It is noted that the Task Based profile model has advantages over the Job Position profile model, however the maxim used at the beginning of this article “One model fits all” should not be applied based on in this article, that is, this article does not recommend and/or establish the Task Based profile model as the best option. The table is merely explanatory between 2 models of the countless existing model alternatives.
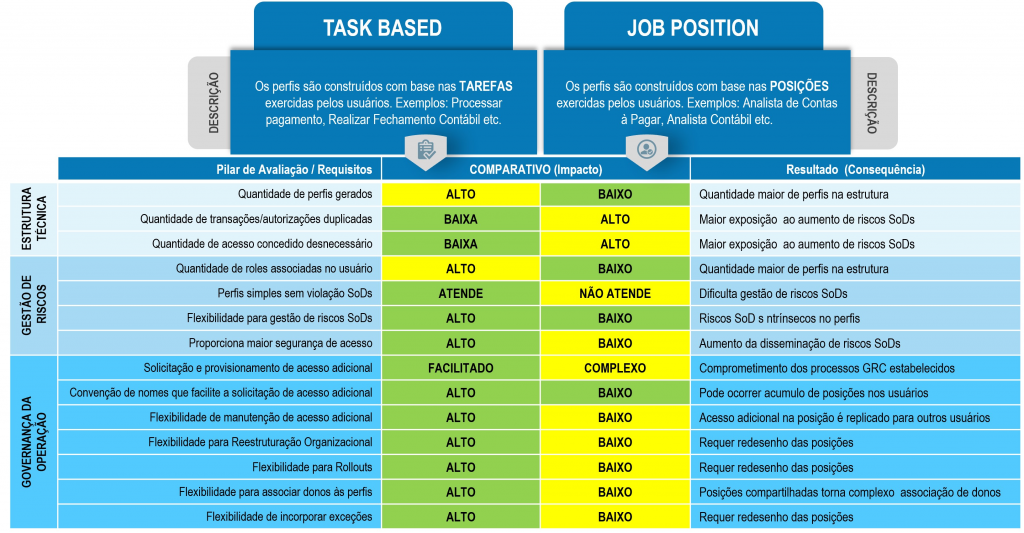
Figure 2: comparison between profile models
There are companies in which the Job Position profile model is the best option due to cultural factors of those involved, industry segment, business, etc. The recommendation is to always seek help from companies specialized in SAP access profiles, so as not to run the risk of adopting an access profile model that is incompatible with the best GRC practices.
But if you haven’t found this company yet, contact us and we guarantee that our services will make a difference.
Sales@trustsis.com | trustsis.com







